Digital Signatures
Digital signatures are the solution to replace wet ink signatures when using digital documents. This concept has been widely adopted and is well integrated into the PDF specification. It is similar to having a public notary stamp in a document that ensures the signatures are legitimate, and the document has not been modified.
The electronic signature essentially captures the intention of the individual to enter into the contract, and the digital signature is used to encrypt the information and confirm the validity of the signed document.
The main benefits of using digital signatures include automating and securing your digital document workflow, saving you time, money, and headaches.
What are the concepts of Digital Signatures?
Usually, digital signatures are used by individuals and organizations in PDF documents to show who checked the document on a specific date/time and that the document has not been updated since it was signed.
There may be one or more signatures in a single PDF document depending on the specifications and the process associated with the signing of a contract. The actual digital signature is a portion of unseen, hashed & encrypted metadata embedded with a certificate in the file.
In addition to the actual digital signature, the PDF file may also include an optional visible representation of the signature. A signature photo and/or a signing certificate summary may be included in the visible portion of the signature.
Hashing
Using a Cryptographic hash function to turn an arbitrary block of data into a fixed-size block of data.
Encryption
- Central Idea
- Transform message before sending
- Transformed message is not readable
- Receiver transforms message back to readable format
- Transforms are done using mathematical functions
- Symmetric Encryption
- Depends on shared key
- Asymmetric Encryption
- Participants have a Private and a Public Key
- Only Public Key is shared
Certificate Authorities
-
A certificate authority (CA) is an entity maintaining and issuing security certificates and public keys that are used in a public network for protected communication. Together with the registration authority (RA), the CA is part of the public key infrastructure (PKI), which verifies the information provided by an electronic certificate requester. If the information is correct, the certificate is verified.
-
Before you use the public key of someone to verify a signature, you need proof that it truly belongs to them. The role of the CA is to issue digital certificates to individuals within a PKI program that shows that a particular public key belongs to a specific individual–so you can claim that digital certificates bind the identity of the individual to their public key. This bond is secured by the CA using the CA's own private key with a digital signature.
-
There are many CAs worldwide, and they can be either enterprise-based, industry-based, national (e.g. linked to e-ID card schemes), or publicly available online. In the case of PDF documents, a list of default CAs is distributed with PDF applications which support digital signatures.
Why use iText & Digital Signatures?
Imagine a document that has legal value. Such a document may contain important information about rights and obligations, in which case you need to ensure its authenticity. You don’t want people to deny the commitments they’ve written down.
Furthermore, this document probably has to be mailed to, viewed, and stored by different parties. At different places in the workflow, at different moments in time, the document can be altered; whether voluntary (for instance, to add an extra signature), involuntary (for example, due to a transmission error), or deliberately, if somebody wants to create a forgery from the original document.
For centuries, we’ve tried to solve this problem by putting a so-called ‘wet ink signature’ on paper.
Nowadays, we can use digital signatures to ensure:
- The integrity of the document— we want assurance that the document hasn’t been changed somewhere in the workflow,
- The authenticity of the document— we want assurance that the author of the document is who we think it is (and not somebody else),
- Non-repudiation— we want assurance that the author can’t deny his or her authorship,
- The timing of signing – we want assurance about the date and time a document was signed,
ISO-32000-2 also introduces a concept that was first published in PAdES-4:
- Long-term validation (LTV): we want the assurance that the integrity, authenticity, non-repudiation, and the time of signing can still be validated in the long term.
These five concepts combined allow you to feel confident that your documents are both secure and correct throughout your workflow.
DIGITAL SIGNING: PDF has been explicitly compatible with embedded electronic signatures for a very long time. Digital signatures can provide a range of valuable capabilities, from tamper protection to authentication and revocation.
FASTER APPROVAL PROCESSES AND SECURITY: Nearly all countries are moving towards a legal framework that recognizes, under certain conditions, the same value to digital evidence as to paper documents. While not all governments are moving at the same pace, the PDF format is encouraged by many legal systems.
What are the architectures of Digital Signatures?
iText has always been at the forefront of digital signatures in PDF by supporting PAdES and being one of the first to support signatures in the latest PDF 2.0 release.
Our mature and easy to use API has been thoroughly tested by the industry and proven to be a success when used throughout several use cases.
Server-side signing
Use Case:
- Company signature: Invoice, Contracts
- Signing services in the Cloud: DocuSign, Adobe Sign
- Security management responsibilities
Client-side signing
Use Case:
- Desktop applications: Adobe Acrobat Pro, Adobe Reader (for Reader-enabled documents, Home-made, e.g. using iText)
- In a web context: The PDF software runs to the client, e.g. using Java Web Start
- Access to the token or smart card through MSCAPI, PKCS#11, Custom smart card library (1 Signature / Second)
- Security: User has smart card and PIN, or USB token and passphrase
Deferred signing
Use Case:
- Signing on an iPad/Tablet: Easy to integrate into a document management system
- ISAE 3000: The standard for assurance over non-financial information
Learning Resources
Read our Digital Signatures ebook, and see code examples.
Adding a digital signature example
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
/*
This file is part of the iText (R) project.
Copyright (c) 1998-2019 iText Group NV
Authors: iText Software.
For more information, please contact iText Software at this address:
sales@itextpdf.com
*/
/*
* This class is part of the white paper entitled
* "Digital Signatures for PDF documents"
* written by Bruno Lowagie
*
* For more info, go to: http://itextpdf.com/learn
*/
package com.itextpdf.samples.signatures.chapter02;
import com.itextpdf.kernel.geom.Rectangle;
import com.itextpdf.kernel.pdf.PdfReader;
import com.itextpdf.kernel.pdf.StampingProperties;
import com.itextpdf.signatures.BouncyCastleDigest;
import com.itextpdf.signatures.DigestAlgorithms;
import com.itextpdf.signatures.IExternalDigest;
import com.itextpdf.signatures.IExternalSignature;
import com.itextpdf.signatures.PdfSignatureAppearance;
import com.itextpdf.signatures.PdfSigner;
import com.itextpdf.signatures.PrivateKeySignature;
import java.io.File;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.IOException;
import java.security.GeneralSecurityException;
import java.security.KeyStore;
import java.security.PrivateKey;
import java.security.Security;
import java.security.cert.Certificate;
import org.bouncycastle.jce.provider.BouncyCastleProvider;
public class C2_01_SignHelloWorld {
public static final String DEST = "./target/signatures/chapter02/";
public static final String KEYSTORE = "./src/test/resources/encryption/ks";
public static final String SRC = "./src/test/resources/pdfs/hello.pdf";
public static final char[] PASSWORD = "password".toCharArray();
public static final String[] RESULT_FILES = new String[] {
"hello_signed1.pdf",
"hello_signed2.pdf",
"hello_signed3.pdf",
"hello_signed4.pdf"
};
public void sign(String src, String dest, Certificate[] chain, PrivateKey pk, String digestAlgorithm,
String provider, PdfSigner.CryptoStandard signatureType, String reason, String location)
throws GeneralSecurityException, IOException {
PdfReader reader = new PdfReader(src);
PdfSigner signer = new PdfSigner(reader, new FileOutputStream(dest), new StampingProperties());
// Create the signature appearance
Rectangle rect = new Rectangle(36, 648, 200, 100);
PdfSignatureAppearance appearance = signer.getSignatureAppearance();
appearance
.setReason(reason)
.setLocation(location)
// Specify if the appearance before field is signed will be used
// as a background for the signed field. The "false" value is the default value.
.setReuseAppearance(false)
.setPageRect(rect)
.setPageNumber(1);
signer.setFieldName("sig");
IExternalSignature pks = new PrivateKeySignature(pk, digestAlgorithm, provider);
IExternalDigest digest = new BouncyCastleDigest();
// Sign the document using the detached mode, CMS or CAdES equivalent.
signer.signDetached(digest, pks, chain, null, null, null, 0, signatureType);
}
public static void main(String[] args) throws GeneralSecurityException, IOException {
File file = new File(DEST);
file.mkdirs();
BouncyCastleProvider provider = new BouncyCastleProvider();
Security.addProvider(provider);
KeyStore ks = KeyStore.getInstance(KeyStore.getDefaultType());
ks.load(new FileInputStream(KEYSTORE), PASSWORD);
String alias = ks.aliases().nextElement();
PrivateKey pk = (PrivateKey) ks.getKey(alias, PASSWORD);
Certificate[] chain = ks.getCertificateChain(alias);
C2_01_SignHelloWorld app = new C2_01_SignHelloWorld();
app.sign(SRC, DEST + RESULT_FILES[0], chain, pk, DigestAlgorithms.SHA256, provider.getName(),
PdfSigner.CryptoStandard.CMS, "Test 1", "Ghent");
app.sign(SRC, DEST + RESULT_FILES[1], chain, pk, DigestAlgorithms.SHA512, provider.getName(),
PdfSigner.CryptoStandard.CMS, "Test 2", "Ghent");
app.sign(SRC, DEST + RESULT_FILES[2], chain, pk, DigestAlgorithms.SHA256, provider.getName(),
PdfSigner.CryptoStandard.CADES, "Test 3", "Ghent");
app.sign(SRC, DEST + RESULT_FILES[3], chain, pk, DigestAlgorithms.RIPEMD160, provider.getName(),
PdfSigner.CryptoStandard.CADES, "Test 4", "Ghent");
}
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
/*
This file is part of the iText (R) project.
Copyright (c) 1998-2019 iText Group NV
*/
/*
* This class is part of the white paper entitled
* "Digital Signatures for PDF documents"
* written by Bruno Lowagie
*
* For more info, go to: http://itextpdf.com/learn
*/
using System;
using System.IO;
using Org.BouncyCastle.Crypto;
using Org.BouncyCastle.X509;
using iText.Kernel.Geom;
using iText.Kernel.Pdf;
using iText.Signatures;
using Org.BouncyCastle.Pkcs;
namespace iText.Samples.Signatures.Chapter02
{
public class C2_01_SignHelloWorld
{
public static readonly string DEST = "../../results/signatures/chapter02/";
public static readonly string KEYSTORE = "../../resources/encryption/ks";
public static readonly string SRC = "../../resources/pdfs/hello.pdf";
public static readonly char[] PASSWORD = "password".ToCharArray();
public static readonly String[] RESULT_FILES =
{
"hello_signed1.pdf",
"hello_signed2.pdf",
"hello_signed3.pdf",
"hello_signed4.pdf"
};
public void Sign(String src, String dest, X509Certificate[] chain, ICipherParameters pk,
String digestAlgorithm, PdfSigner.CryptoStandard subfilter, String reason, String location)
{
PdfReader reader = new PdfReader(src);
PdfSigner signer = new PdfSigner(reader, new FileStream(dest, FileMode.Create), new StampingProperties());
// Create the signature appearance
Rectangle rect = new Rectangle(36, 648, 200, 100);
PdfSignatureAppearance appearance = signer.GetSignatureAppearance();
appearance
.SetReason(reason)
.SetLocation(location)
// Specify if the appearance before field is signed will be used
// as a background for the signed field. The "false" value is the default value.
.SetReuseAppearance(false)
.SetPageRect(rect)
.SetPageNumber(1);
signer.SetFieldName("sig");
IExternalSignature pks = new PrivateKeySignature(pk, digestAlgorithm);
// Sign the document using the detached mode, CMS or CAdES equivalent.
signer.SignDetached(pks, chain, null, null, null, 0, subfilter);
}
public static void Main(String[] args)
{
DirectoryInfo directory = new DirectoryInfo(DEST);
directory.Create();
Pkcs12Store pk12 = new Pkcs12Store(new FileStream(KEYSTORE, FileMode.Open, FileAccess.Read), PASSWORD);
string alias = null;
foreach (var a in pk12.Aliases)
{
alias = ((string) a);
if (pk12.IsKeyEntry(alias))
break;
}
ICipherParameters pk = pk12.GetKey(alias).Key;
X509CertificateEntry[] ce = pk12.GetCertificateChain(alias);
X509Certificate[] chain = new X509Certificate[ce.Length];
for (int k = 0; k < ce.Length; ++k)
{
chain[k] = ce[k].Certificate;
}
C2_01_SignHelloWorld app = new C2_01_SignHelloWorld();
app.Sign(SRC, DEST + RESULT_FILES[0], chain, pk, DigestAlgorithms.SHA256,
PdfSigner.CryptoStandard.CMS, "Test 1", "Ghent");
app.Sign(SRC, DEST + RESULT_FILES[1], chain, pk, DigestAlgorithms.SHA512,
PdfSigner.CryptoStandard.CMS, "Test 2", "Ghent");
app.Sign(SRC, DEST + RESULT_FILES[2], chain, pk, DigestAlgorithms.SHA256,
PdfSigner.CryptoStandard.CADES, "Test 3", "Ghent");
app.Sign(SRC, DEST + RESULT_FILES[3], chain, pk, DigestAlgorithms.RIPEMD160,
PdfSigner.CryptoStandard.CADES, "Test 4", "Ghent");
}
}
}
Digitally sign and encrypt your PDF documents with iText Core
Download iText Core from our download hub or try out the full iText Suite.
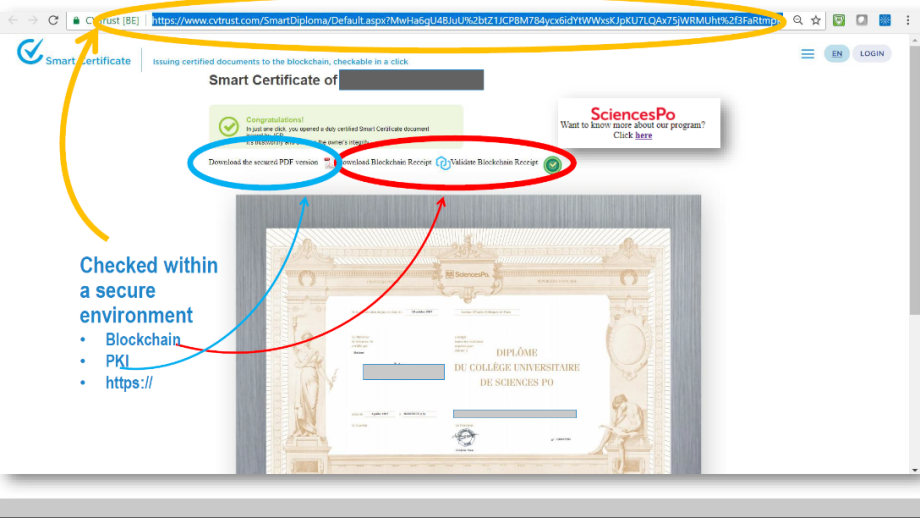
CVTrust developed their Smart Certificate platform which enables institutions to digitally issue and share certified and trusted documents, which are checkable in a click.
- Smart Certificate 2.0 offers many improvements such as an enhanced user experience and UI, additional features, and is designed to be available as a SaaS (Software as a Service) that can be used by any organizations to issue certified and verifiable documents, whatever their purpose. It also provides an extremely advanced level of data encryption as well as complying with GDPR and privacy requirements.
- Smart Certificate 2.0 also guarantees the validity of documents issued using the platform. At any time, a qualification or other accreditation can be verified by clicking a link or scanning a QR code. This ensures that anyone who claims they have attained a qualification can be proven to have done so.
- For one of their largest Belgian customers, CVTrust needed to use the GlobalSign API to generate the certificates required for digital signatures. In order to achieve this, it was necessary to integrate iText Core into the Smart Certificate back-end. The new solution using iText Core and the GlobalSign API needed to extend the capabilities of the Smart Certificate platform, while also being easy to integrate into the existing infrastructure.
-
iText Core enables the mass generation of the required PDF documents, and also handles the addition and appearance of digital signatures within the PDF. When a Smart Certificate is being awarded, the Smart Certificate platform creates a unique PDF based on a pre-existing PDF template. Then, using the GlobalSign API a verified digital signature is added to the document.
-
At the same time, a unique hash of the PDF is also generated and sent to the Woleet servers, in order for the hashes to be securely stored in the blockchain. CVTrust uses blockchain technology to enhance document security and make it virtually impossible to falsify, as any changes to the hash would have to be replicated across all the nodes of the blockchain.
All of this means documents are:
- Accessible in a click (including their blockchain hash/verification)
- Downloadable with a click
- Shareable with a click, e.g. on LinkedIn
- Checkable in a click (via a link/QR code), to guarantee the integrity, authenticity and validity of each document
Use Case: Digital Signatures Simplified for Consumers and Businesses with Release of eaZySign
- Zetes, which provides user identification solutions and Belgian eIDs, has launched a cloud-based digital signature platform that simplifies how businesses and consumers can replace hand-written signatures with electronic versions. The cloud-based platform provides any-device accessibility – web, computer or mobile – and gives businesses faster time to revenue, greater cost savings, and an improved customer experience.
- In partnership with iText, the provider of the world’s most widely used PDF development library, and GlobalSign, a leading provider of identity and security services, Zetes developed the eaZySign solution. The new eaZySign platform solves two of the most common challenges to digital signature adoption by making it easy to manage and apply digital signatures while ensuring the signatures maintain the appropriate level of trust and legality.
- EaZySign is customizable to support a wide range of application needs. It is platform and operating system agnostic, allowing the signing process to be performed via web portals, desktops, and the most popular mobile platforms (iOS, Android) for easy access by end users.
- The signatures rely on Belgian electronic identity cards (e-ID) or GlobalSign PKI-based credentials and comply with PDF Advanced Electronic Signatures (PAdES) standards, as established by the European Telecommunications Standards Institute (ETSI).
Mass Consumer Adoption: iText’s in-depth knowledge in encryption has led to a combination where ease-of-use and security empower the eaZySign platform, making it more acceptable for mass consumption.
PDF Digital Signing Workflows Around Company Processes: iText was used to create the digital signing workflows, which are embedded in the eaZySign solution. Users can simply upload documents to the platform, making them available to end users for signing.
Digital Signing Certificate and PAdES Compliance: GlobalSign is a trusted timestamp authority (TSA) and provides the time stamping services required for the digital signatures created in eaZySign to meet all PAdES conformance levels. It also includes a third-party timestamp to verify when the document was created and supports non-repudiation.

